how can doc file be detected as trojan
Trojans often use the same file names as real and legitimate apps. More specifically McAfee quarantined the HTML PNG and some other files the Trojan created after the macro was run.
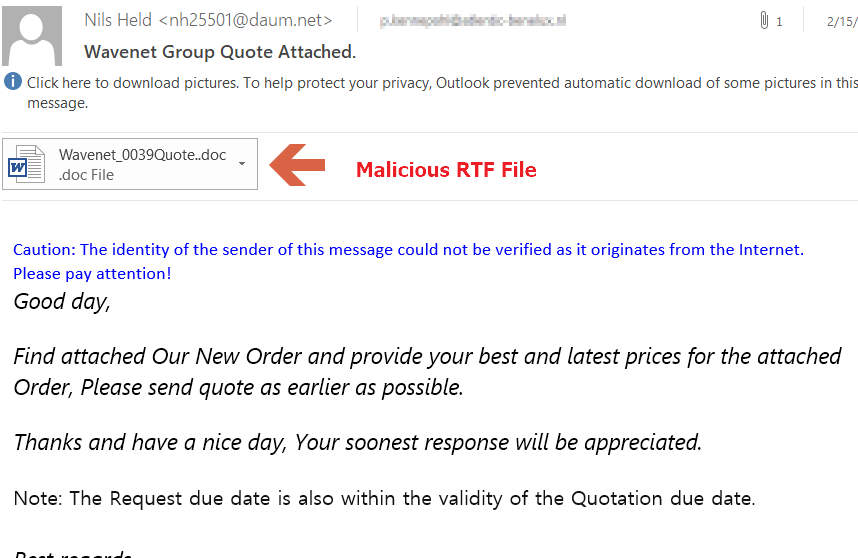
Wave Of Spam Uses Rtf Exploit Delivers A Trojan Spyware Official Juniper Networks Blogs
If you want to detect suspicious content ie.
. Alternatively send in one of your detected files as false positive submission to one of the AVs that detect them. You can try to detect the data loss. The scan engine did not detect the word document or the actual virus.
See this link for directions to that file. Well theres probably no 100 way to be certain but most well-known trojans will have undergone extensive analysis and AV solutions in the market will do their best to remove them. In this case spam email is likely to be the culprit.
When the tool opens. So you have the Backup Setup active on your PC. JavaScript manually you can start with any hex editor and then you can write your own yara rules if its needed.
You can copy the error and find out about the affected exe file online. It may also be causing the same re-detection for your Trojan. Trojans find their way onto computers by hiding in software downloads making them easy to unintentionally install.
Virus detection is one of the intelligence tasks in Filestack platform. Download and install other malware such as viruses or worms. In addition to spotting known trojans the McAfee antivirus program can identify new trojans by detecting suspicious activity inside any and all of your applications.
It will be your. Now you can restore your data objects with the. This task is only available at Filestack Workflows.
An IP trackback service will track the IP address of any machine that downloads and opens the malicious Excel file. Yet this approach works only if Backup Settings are active on your computer. Your antivirus program would show regular updates about having removed a threat.
1 level 2 Laura-Lau. Of course if JavaScript is present that doesnt mean it has to be malicious but it can be a subject of further investigating. Using this mechanism you can detect infected content in files your users upload asynchronously immediately after file hit the storage.
Windows XP users double-click on the file. Read more about Workflows here. It is easy to accidentally download a trojan thinking that it is a legitimate app.
Disable the function of System restore. Recover Files from Trojan Attack without Software. Usually most viruses tend to set entries with random names in the Run and RunOnce sub-keys.
It even works for encrypted files. Usually if the document file is opened by an unsuspecting user the embedded code is silently launched and run on the machine. The Trojan horse virus can infect a computer or a mobile device without being notice and it could remain for a long period of time especially if the victim doesnt know.
If the file is opened embedded code will either drop and install a harmful program onto the users device or will download additional harmful components from a remote site to install. By detecting suspicious activity inside your applications the McAfee antivirus program can also identify new trojans in addition to detecting known ones. See here for Sophos analysis on their TrojDocDl-AEE detection.
After recognizing a file infected with Trojan horse it becomes easy to remove. You need Sophos Virus Removal Tool which I used or Microsoft safety scanner mentioned above. 2 Hold CTRLF keys and type TrojanGeneric or the file name of the malicious executable of the virus which is usually located in AppData Temp Local Roaming or SystemDrive.
This trojan is known as Grace Wire or Flawed Grace. Trojans can come in many different varieties but generally they do the following. Windows Defender on Windows 7 provides Anti-Spyware protection only.
Search in header of file for. An effective antivirus program searches for valid trust and app behavior as well as trojan signatures in files in order to detect isolate and then promptly remove them. TrojdocDl-AEE is not detected by McAfee or defender.
It can be of almost any file type but most likely its a Doc file. Part of the malicious VBScript creates a fake document on the fly that is displayed to the user. Lets take a closer look.
Either your system is infected or you use some specific settings that create false positive detections. The documents also include malware downloaders that deliver Dridex and Trick banking trojans. Eliminate the notifications by deleting it in the Detection History file.
You can also get a trojan horse by visiting an insecure. The file is concealed as mozillaexe and periodically checks with its command and control infrastructure. Answer 1 of 5.
Lastly once you have file downloaded on computer make sure you have real time anti-malware protection. Sometimes antivirus programs detect and delete TrojanDownloader repeatedly and constantly. The RAT can then steal information from the system.
This detection indicates that the detected file is a phishing-trojan - a document file that is designed to look legitimate but actually serves as a delivery vehicle for harmful programs. We can easily extract the code with the help of the same toololedumppy -s -v Lets fetch all of themoledumppy -s 7 -v 523-Invoice 7500005791doc. Most of the time your system will give you a DLL error which is associated with the Trojan attack.
You can even scan the file before even downloading using online virus scanners. In order to find out you can upload one of those detected files to Virustotal and post the Virustotal link. The document file may have been deliberately created to include harmful embedded code or it may be a legitimate document file that has been tampered with by an unauthorized party to insert the unwanted content.
While commercial RATs can be used for legitimate purposes malicious actors often abuse them for their own sinister goals. The analysis should begin as soon as possible. Right-click FRSTFRST64 and select Run as administrator.
However the most important part is in the attachment. If the trojan is relatively new you can use a customized removal. There is an online tool called PDF Examiner which can analyse PDF files for Javascript obfuscation and other known exploits.
How Do I Know If A File Has A Virus. A trojan horse is a type of malware that can infect any computer. This is the point where we can expect some illegitimate functionalities macros can potentially deploy malicious actions.
You can upload up to 128MB of files. Use the infected device for click. Trojan horse virus is a malicious software program that is capable of damaging any computer.
This has been found to be true for PUPs PUA. I suspect because they had ENCRYPT in the filename or had a signature similar to previous crypto locker files. If you receive a SmartScreen warning click on More Info and Run Anyway.
And select a suitable backup to recover your files. If you can see the Trojan in Windows Defender Protection History you can.

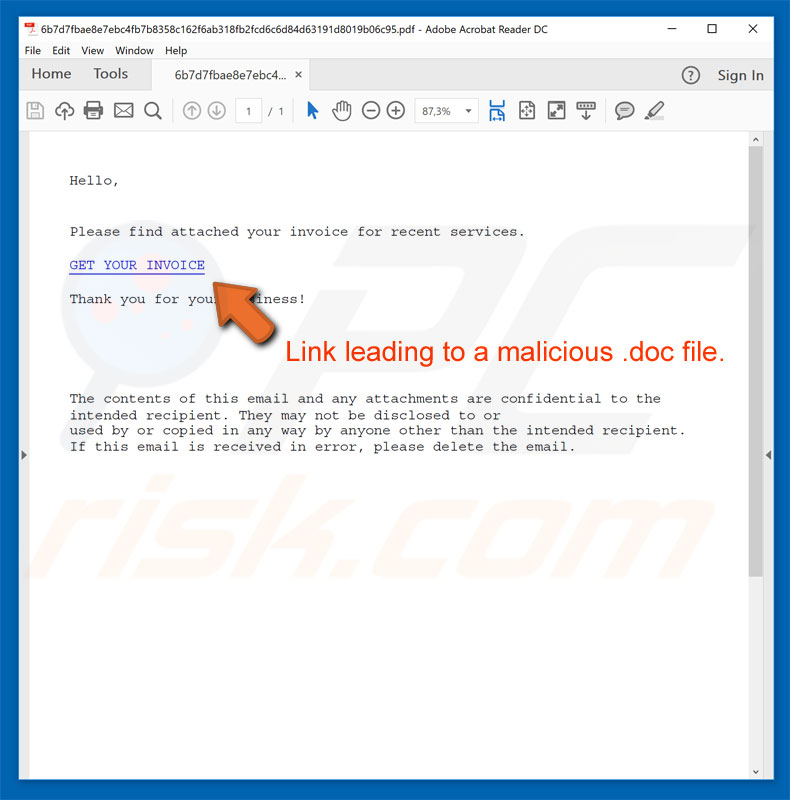
Trojandownloader Pdf Domepidief A Virus Malware Removal Instructions Updated

Emotet Returns In Summer 2020 With New Improvements Infosec Resources

Decoy Microsoft Word Document Delivers Malware Through A Rat

Remove Inquiry Doc Virus From Mac Macsecurity
Can I Get A Computer Virus By Opening A Doc File Quora

Editable Cyber Security Incident Response Plan Template Doc Example Report Template Incident Report Form Security Report
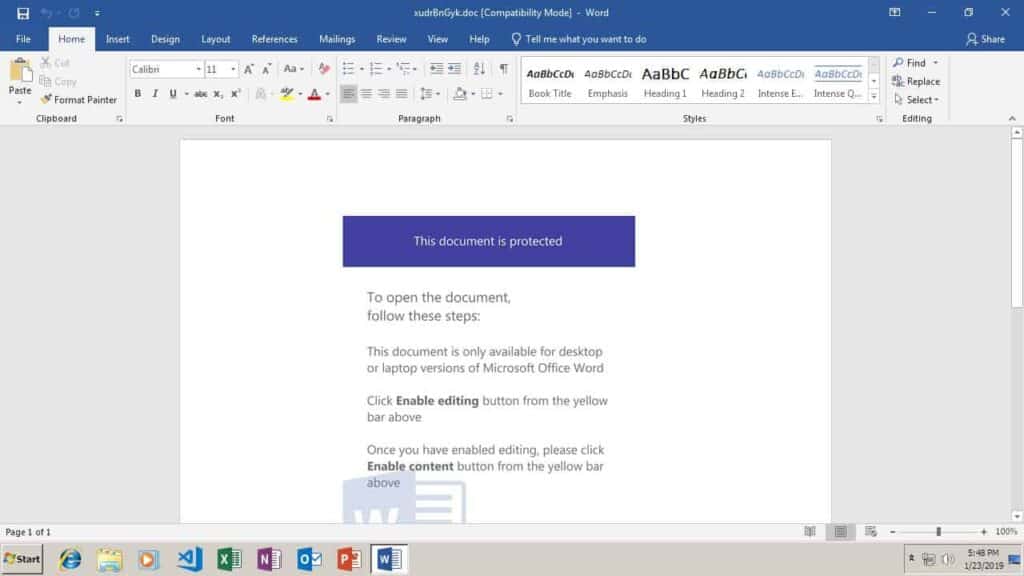
Emotet Malspam Campaign Exploits Reliance On Magic For File Type Detection Seanthegeek Net

Editable Cyber Security Incident Response Plan Template Doc Example Report Template Incident Report Form Security Report

Opening Of A Normal Doc File Using The Original Winword Exe Left And Download Scientific Diagram
Is There A Safe Way To Open A Suspect Docx Document On A Computer Can One Safely Save It Before Scanning Quora
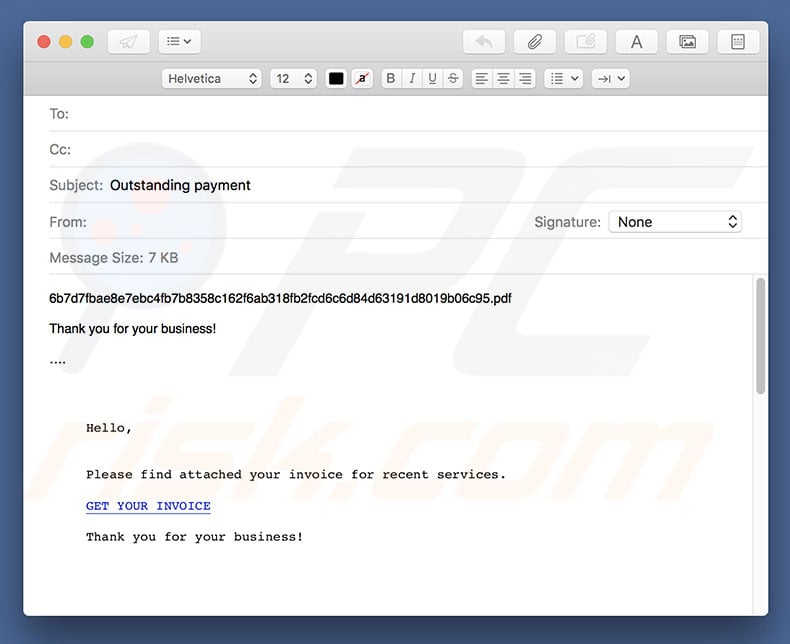
Trojandownloader Pdf Domepidief A Virus Malware Removal Instructions Updated

Doc File Virus Removal Restore Doc Files

Opening Of A Normal Doc File Using The Original Winword Exe Left And Download Scientific Diagram
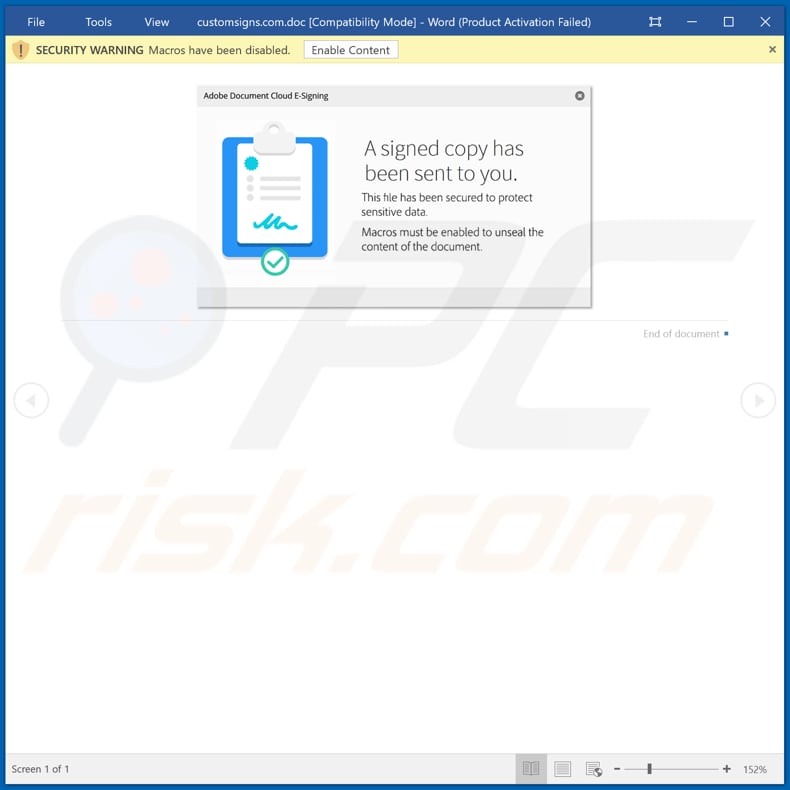
Adobe Document Cloud E Signing Email Virus Removal And Recovery Steps Updated

Remove Inquiry Doc Virus From Mac Macsecurity
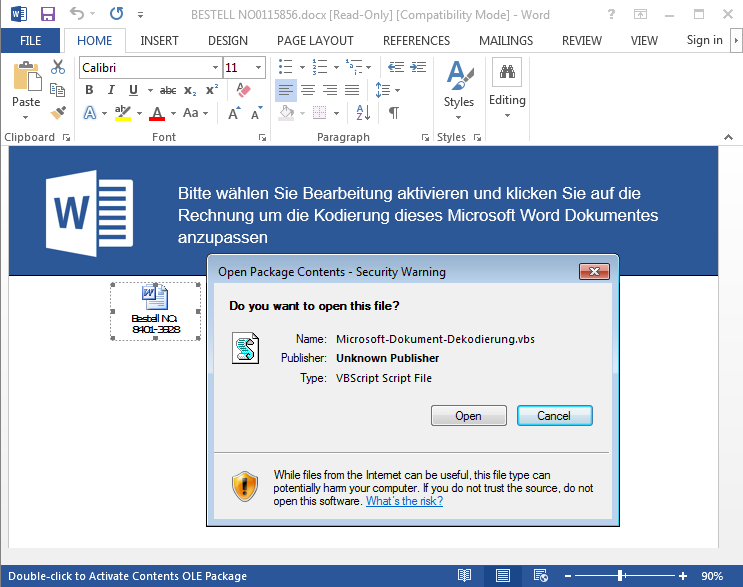
Dridex An Old Dog Is Learning New Tricks G Data

Where S The Macro Malware Authors Are Now Using Ole Embedding To Deliver Malicious Files Microsoft Security Blog

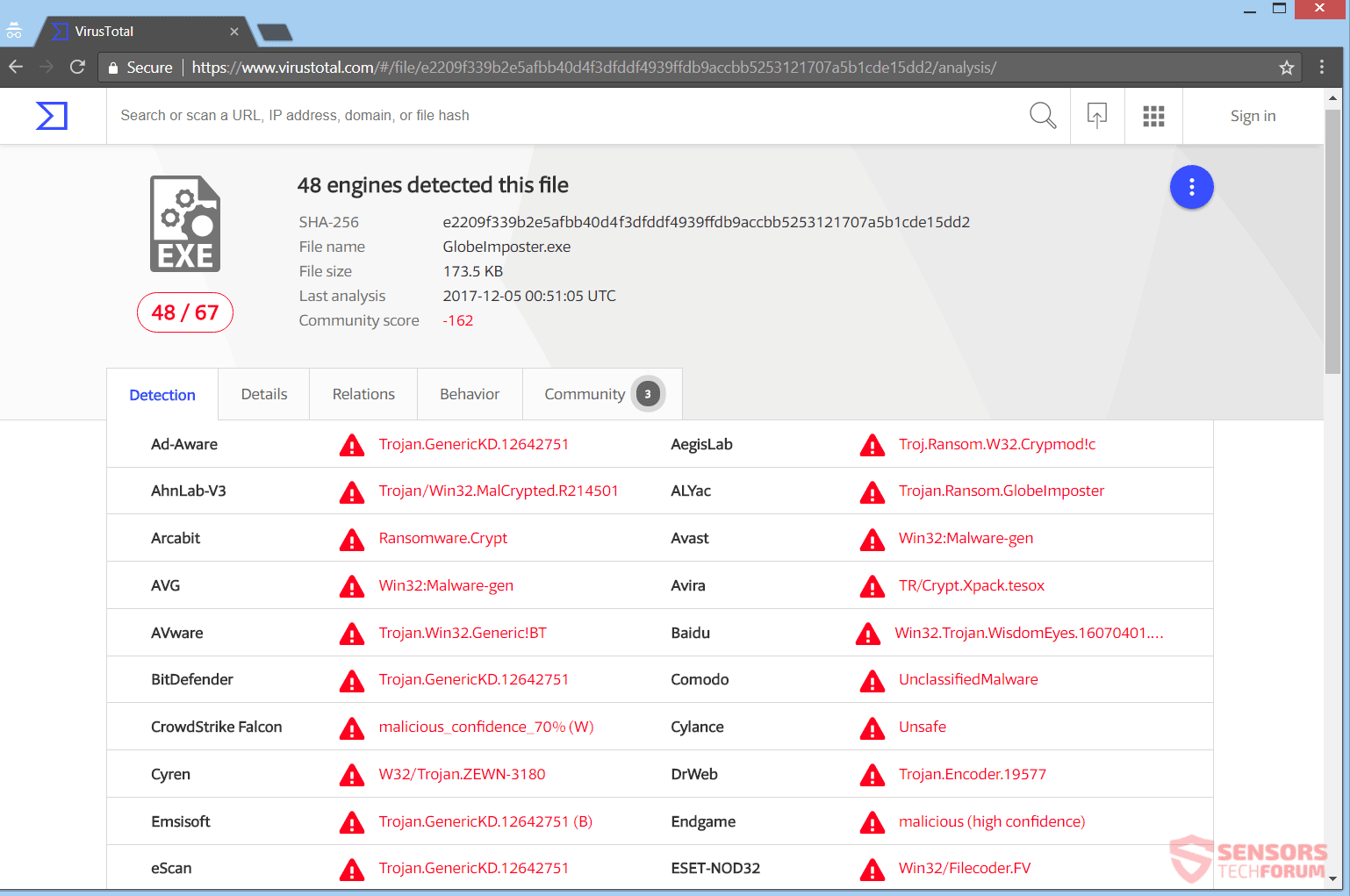
0 Response to "how can doc file be detected as trojan"
Post a Comment